Modern attacks combine DDoS floods, DNS manipulation, and firmware compromises. This is how I built a SafeDeepAgent-hardened, multi-agent security mesh that can see the whole campaign instead of isolated symptoms.
Modern DDoS campaigns don't just hit your network. They bend DNS, ride on compromised firmware, and weaponize whole device fleets. I built DDoS Sentinel Agent, a multi-agent, SafeDeepAgent-hardened AI system that watches network traffic, DNS behavior, and supply-chain releases together and responds like a coordinated security mesh.
The Problem: Attacks Are Multi-Vector, Defenses Are Not
Modern cyber attacks don't look like single events anymore. They look like coordinated campaigns — floods of DDoS packets, DNS distortion, and compromised firmware updates happening all at once.
Most security tools still try to defend against them one domain at a time:
- "That's a network DDoS issue."
- "That's a DNS anomaly."
- "That's a firmware incident."
But attackers don't care about your org chart.
The last few years have been a brutal reminder that the internet's nervous system is fragile. Botnets like Aisuru have been able to:
- Launch 15–22 Tbps DDoS attacks
- Abuse DNS popularity rankings
- Ride on firmware supply-chain compromises
- Assemble hundreds of thousands of compromised devices into one coordinated weapon
So I asked a simple question:
What if we treated modern DDoS campaigns as multi-vector systems — and defended them with multi-agent systems?
That question became DDoS Sentinel Agent: a multi-agent security mesh built on top of my secure agentic AI framework, SafeDeepAgent.
This article is the story of how it evolved from a single DDoS detector into a coordinated mesh of agents watching network traffic, DNS behavior, and supply-chain releases together.
Why a Single DDoS Detector Is No Longer Enough
Most "DDoS detection" tools still focus on network-layer symptoms:
- PPS (packets per second) spikes
- UDP floods
- Unusually high connection counts
That's necessary — but now it's incomplete.
Real campaigns like Aisuru combine at least three domains:
1. Network DDoS
- Massive UDP floods (95%+ of traffic)
- 100k–300k+ PPS
- Thousands of distributed IoT bots
2. DNS Manipulation
- Resolver abuse (e.g. hammering public resolvers like 1.1.1.1)
- Artificial "popularity" to distort rankings
- DNS QPS that doesn't match real HTTP usage
3. Supply-Chain Compromise
- Malicious firmware updates (TotoLink-style server breaches)
- Unknown or compromised signing keys
- Worm-like rollouts to tens of thousands of devices
If you only stare at network traffic, you see "a big spike." If you only stare at DNS, you see "weird QPS." If you only stare at supply-chain, you see "suspicious update behavior."
You don't necessarily see the campaign.
That's exactly the gap DDoS Sentinel Agent tries to close.
DDoS Sentinel Agent in One Sentence
DDoS Sentinel Agent is a multi-agent security mesh that coordinates specialized AI agents across network, DNS, and supply-chain domains to detect Aisuru-style multi-vector attacks — all wrapped in SafeDeepAgent's 12 security foundations and 13-layer defense model.
Today the system runs on Python 3.10+ and is built as a real package, not a throwaway script, with:
- A Network (DDoS) Agent
- A DNS Integrity Agent
- A Supply-Chain Guardian Agent
- A Security Mesh Orchestrator
- And a full SafeDeepAgent security wrapper around all actions
The Architecture: From Single Agent to Security Mesh
Phase 1 — Single DDoS Agent
The original version of DDoS Sentinel Agent was a single-domain DDoS detector.
It would:
- Ingest raw packets or simulated traffic
- Extract features like:
- PPS (packets per second)
- UDP ratio
- Unique source IPs
- Packet size distribution
- Run a combination of:
- Signature checks (e.g.
UDP ratio ≥ 95%) - Baseline-aware anomaly detection
- Produce:
- Severity levels (
NONE / LOW / MEDIUM / HIGH / CRITICAL) - Recommended mitigations (rate limiting, IP blocking, etc.)
That worked well — but it was blind to what was happening in DNS and the firmware layer.
So I pushed it further.
Phase 2 — Multi-Agent Mesh
The new architecture introduces three domain agents and a mesh that coordinates them.
1. Network Agent (DDoSSentinelAgent)
Focus: Aisuru-style DDoS patterns.
Detects:
- Massive UDP floods (≥ 95% UDP)
- Extreme packet rates (≥ 100k PPS)
- Botnet patterns (≥ 3,000 unique source IPs)
- Amplification (small packets + huge volume)
- Focused targeting (low destination IP entropy)
- Deviations from baseline (3σ and beyond)
2. DNS Integrity Agent (DNSIntegrityAgent)
Focus: DNS abuse & popularity manipulation.
Detects:
- Artificial jumps in DNS query volume (QPS)
- Abnormal ASN or client IP distributions
- Domains with high DNS QPS but very low HTTP traffic
- Resolver abuse patterns (e.g. hammering shared public resolvers)
Think: "Aisuru gaming the top domains list by spamming DNS resolvers."
3. Supply-Chain Guardian Agent (SupplyChainGuardianAgent)
Focus: Firmware & release attacks.
Detects:
- Releases signed with unknown or suspicious keys
- Unusual build hosts
- Fast, worm-like rollout patterns
- Post-release device behavior anomalies:
- Huge jumps in outbound traffic
- Sharp increase in C2-like connections
Think: "TotoLink firmware server breach → malicious update → devices conscripted into DDoS."
4. SecurityMeshOrchestrator
The orchestrator sits above them and acts as the "brain of brains":
- Feeds each agent only its relevant observations
- Collects each agent's
AnalysisResult - Runs cross-domain correlation, for example:
Network CRITICAL + DNS HIGH + Supply-Chain CRITICAL → Global CRITICAL incident
- Produces a unified mitigation plan:
- Rate-limiting rules
- DNS sinkholing or de-ranking
- Firmware rollback and key revocation
- Human escalation paths
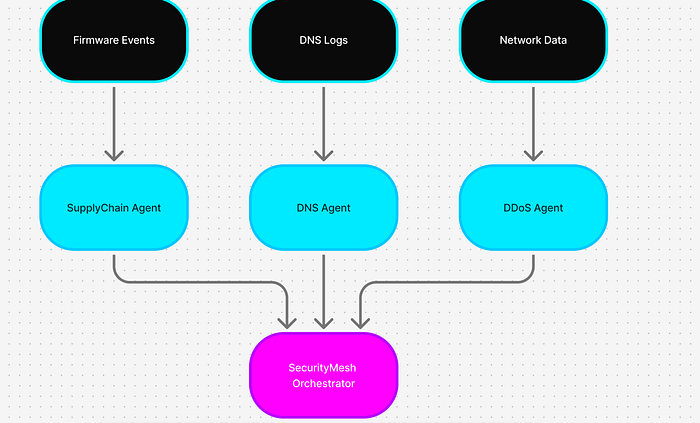
Conceptually, the system looks like this:
+----------------------------+
| SecurityMesh |
| (Orchestrator + Fusion) |
+------------+---------------+
|
--------------------------------------------------------
| | |
+-----------+ +-------------+ +-------------------+
| DDoS Agent| | DNS Agent | | SupplyChain Agent |
+-----------+ +-------------+ +-------------------+
| | |
v v v
traffic logs DNS logs firmware eventsEach agent sees its own world. The mesh sees the campaign.
Who Secures the Security Agents? SafeDeepAgent.
There's a bigger question behind all of this:
If we're going to use AI agents for security, who secures the agents?
That's what SafeDeepAgent is for.
DDoS Sentinel Agent doesn't just use AI. It runs inside a defensive AI framework that enforces 12 security foundations:
- ✅ Action Validation — validate every tool/action call
- ✅ Memory Firewalls — risk-scored data access boundaries
- ✅ Provenance Tracking — end-to-end lineage for inputs and outputs
- ✅ Execution Sandboxing — isolated execution for risky operations
- ✅ Behavioral Monitoring — watch agents for abnormal decisions
- ✅ Meta Supervision — a higher-level supervisory agent
- ✅ Audit Logging — every decision goes to a tamper-evident log
- ✅ Purpose Binding — agents can't drift out of their scope
- ✅ Intent Tracking — ensure action sequences match goals
- ✅ Deception Detection — guardrails against manipulated input
- ✅ Risk Adaptation — raise or lower autonomy based on risk
- ✅ Human Governance — critical actions require approval
Every domain agent — DDoS, DNS, supply-chain — routes its work through:
result = safe_agent.execute_safe_action({
"tool": "ddos_detection", # or "dns_analysis", "supply_chain_scan"
"parameters": {
"packets": packets,
"timestamp": datetime.now().isoformat()
}
})If SafeDeepAgent decides an action is unsafe, out of scope, or suspicious, it can:
- Block it
- Down-scope it
- Escalate it to a human
The Security Mesh Orchestrator is also governed by SafeDeepAgent, especially for global actions like:
- Modifying firewall policies
- Triggering mass firmware rollbacks
- Escalating to production incident channels
So you don't just get agents that detect attacks. You get agents that are themselves defended.
Aisuru-Style Multi-Vector Attack Demo
To show the whole mesh in action, I built a five-phase synthetic scenario that mirrors an Aisuru-like campaign.
Once the project is installed, you can run:
python scripts/cli.py mesh-demoThe scenario unfolds like this:
Phase 1 — Normal baseline
Network, DNS, and supply-chain all look clean.
Phase 2 — DDoS begins
180k PPS UDP flood, thousands of unique IPs.
Phase 3 — DNS manipulation
Resolver spam, suspicious QPS, low HTTP correlation.
Phase 4 — Firmware compromise
Unknown signing key, suspicious build host, aggressive rollout.
Phase 5 — Mesh correlation
The orchestrator fuses all signals into one CRITICAL multi-vector incident and produces a unified mitigation plan.
The output looks like this (simplified):
[NETWORK] CRITICAL: Detected 180k PPS UDP flood with 6000 unique IPs.
[DNS] HIGH: Sudden spike in QPS, domain popularity manipulation via resolver spam.
[SUPPLY_CHAIN] CRITICAL: Unsigned firmware v3.0.0 from suspicious host
distributed to 55k devices.
[MESH] CRITICAL: Multi-vector coordinated attack detected.
[MESH] Attack Pattern: DDoS + DNS abuse + Supply-chain compromise (Aisuru-style)
[MESH] Recommended actions:
- Rate limit UDP traffic > 50k PPS
- Sinkhole suspicious domains
- Roll back firmware v3.0.0
- Notify security operationsThat's exactly the behavior I wanted:
- Each agent sees its own local problem.
- The mesh sees the campaign.
Multi-Agent Mesh API (Code You Can Copy)
Everything is exposed as a clean Python API. You can build your own mesh like this:
from ddos_sentinel import (
SecurityMeshOrchestrator,
DDoSSentinelAgent,
DNSIntegrityAgent,
DNSObservation,
SupplyChainGuardianAgent,
SupplyChainObservation,
TrafficSimulator
)
from safedeepagent.core.safe_agent import SafeDeepAgent, SafeConfig
# Initialize SafeDeepAgent
safe_agent = SafeDeepAgent(safe_config=SafeConfig())
# Build the mesh
mesh = SecurityMeshOrchestrator(
agents=[
DDoSSentinelAgent(sensitivity=0.8),
DNSIntegrityAgent(sensitivity=0.8),
SupplyChainGuardianAgent(sensitivity=0.8),
],
safe_agent=safe_agent,
)
# Generate observations
simulator = TrafficSimulator(seed=42)
observations = {
"network": simulator.generate_aisuru_ddos_traffic(
duration_seconds=60,
attack_pps=150_000,
botnet_size=5000,
),
"dns": DNSObservation(
domain="target.com",
qps=7500.0,
unique_client_ips=3000,
asn_distribution={"AS6666": 2100, "AS7777": 600},
query_types={"A": 7000, "AAAA": 400},
http_traffic_ratio=0.05, # Low = fake queries
),
"supply_chain": SupplyChainObservation(
release_id="v3.0.0",
version="3.0.0",
signing_key_id="KEY_UNKNOWN",
build_host="suspicious-host.net",
rollout_speed=30_000.0,
total_devices_updated=50_000,
deployment_duration_hours=1.5,
post_release_traffic_multiplier=15.0,
is_known_signing_key=False,
build_host_reputation="suspicious",
device_behavior_anomalies=12_000,
),
}
# End-to-end analysis through the mesh
decision = mesh.run_end_to_end(observations)
print("Global Severity:", decision["summary"]["global_severity"])
print("Affected Domains:", decision["summary"]["affected_domains"])
print("Recommended Actions:", decision["global_plan"].action_count())This detects the coordinated multi-vector attack and gives you one mitigation plan, not three disconnected alerts.
Still Want Just a DDoS Detector? You Can Do That Too.
If you only care about network DDoS, the single-agent interface still exists:
from ddos_sentinel import DDoSSentinelAgent, TrafficSimulator
agent = DDoSSentinelAgent(sensitivity=0.8, window_size_seconds=10)
simulator = TrafficSimulator(seed=42)
packets = simulator.generate_aisuru_ddos_traffic(
duration_seconds=60,
attack_pps=150_000,
botnet_size=5000,
)
result = agent.run_ddos_detection(packets)
if result["success"] and result["analysis"].attack_detected:
summary = agent.summarize_findings()
print(summary["summary"])
mitigation = agent.propose_mitigation()
for action in mitigation["immediate_actions"]:
print(" •", action)You can adopt this incrementally:
- Start with one agent.
- Add DNS.
- Add supply-chain.
- Turn on the full Security Mesh when you're ready.
Under the Hood: System Components
Internally, the repo is structured like a real product, not a toy:
core/– Shared types and base agent interfacesagent/– Network (DDoS) agentdns/– DNS integrity agentsupply_chain/– Supply-chain guardian agentmesh/– Orchestrator & correlation enginedata/– Traffic simulation and feature extractiondetection/– Aisuru signatures andDDoSDetectionEnginescripts/– CLI entrypointstests/– Full test suite, including mesh tests
That separation is intentional: it should be easy to add more agents:
- Identity agent
- API abuse agent
- WAF/HTTP abuse agent
- SIEM integration agent
All of them living under the same SafeDeepAgent security umbrella.
Where This Goes Next
The current version already supports:
- Multi-vector detection across network, DNS, and supply-chain
- Cross-domain correlation
- Unified mitigation planning
- SafeDeepAgent-wrapped actions and meta-supervision
- Simulation, testing, and CLI demos
The roadmap (documented in ROADMAP.md) includes:
- Real-time PCAP ingestion
- Distributed, multi-node mesh
- ML-based anomaly detection for each domain
- SIEM integration (Splunk, Sentinel, etc.)
- Cloud-native deployment patterns
In other words:
From local mesh → distributed, cloud-scale autonomous security fabric.
How to Try It Yourself
Clone and install:
git clone https://github.com/oluwafemidiakhoa/DDoSSentinelAgent.git
cd DDoSSentinelAgent
pip install -r requirements.txt
# or
pip install -e .Run the multi-vector mesh demo:
python scripts/cli.py mesh-demoRun focused scenarios:
python scripts/cli.py demo-mesh --scenario clean
python scripts/cli.py demo-mesh --scenario network_attack
python scripts/cli.py demo-mesh --scenario dns_abuse
python scripts/cli.py demo-mesh --scenario supply_chain_compromise
python scripts/cli.py demo-mesh --scenario multi_domainRun tests:
pytest
pytest --cov=ddos_sentinel --cov-report=htmlFinal Thoughts
DDoS Sentinel Agent is not just another DDoS tool.
It's a working example of what happens when you combine:
- Secure agentic AI (SafeDeepAgent)
- Multi-domain signals (network, DNS, supply-chain)
- A real adversary mental model (Aisuru-style campaigns)
And you treat defense as a multi-agent system, not just a pile of signatures.
If you're building in:
- AI security
- Agentic infrastructure
- Autonomous SOC tooling
- Defensive AI frameworks
I'd love for you to explore the repo, break it, extend it, and build on top of it.
👉 Repo: https://github.com/oluwafemidiakhoa/DDoSSentinelAgent
You're very welcome to cite or fork it in your own research and experiments.