⚠️ Disclaimer: Tools and techniques discussed in this blog is only meant for educational, ethical OSINT & vulnerability research purposes. Author not responsible for any misuse!
New to UrlScan Dorking ? Check from beginning 👇
🌐 Site: urlscan[.]io
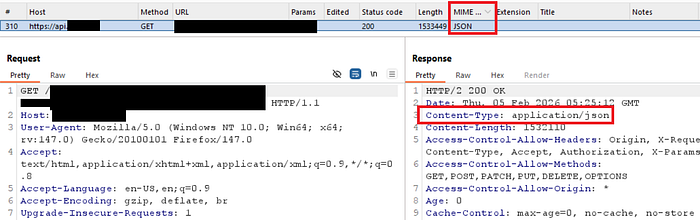
1️⃣ Finding endpoints based on MIME TYPE
- Might lead to PII leak + fuzzing this with good wordlists
domain:example.com AND page.mimeType:"application/json"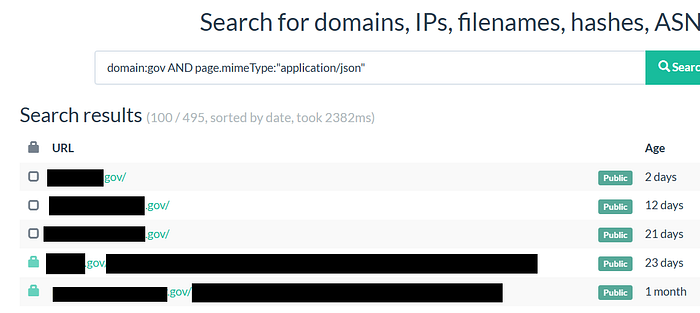
Choosing good wordlists (Assetnote)
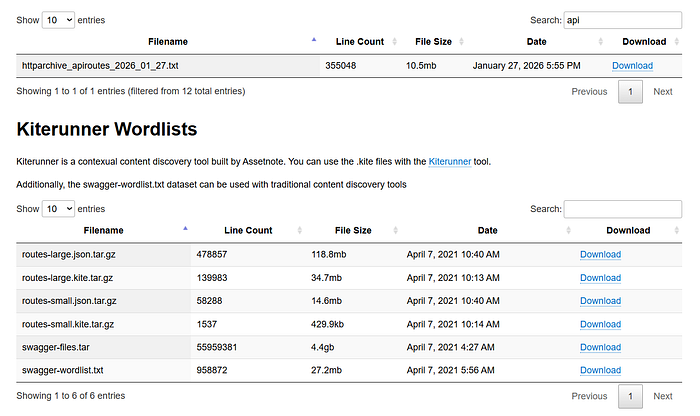
No results ? Then use cewl and make a customized wordlists.
2️⃣PDF Files
- Might lead to internal docs exposed
page.mimeType:"application/pdf" AND domain:example.com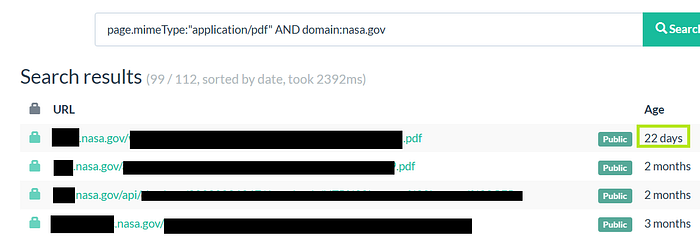
Not all available files are indexed. From here we get to know which subdomain needs further deep dive recon.
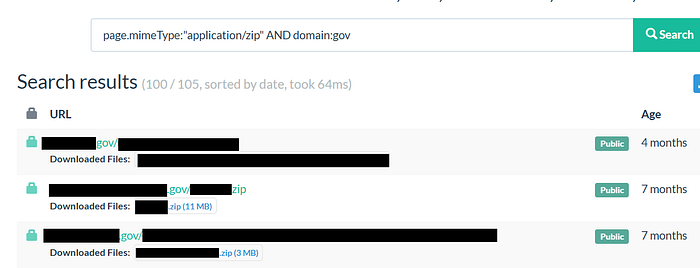
3️⃣ ZIP Files
- Might lead to source code or backup files disclosure
4️⃣ Reverse DNS Recon
page.ptr:domain.com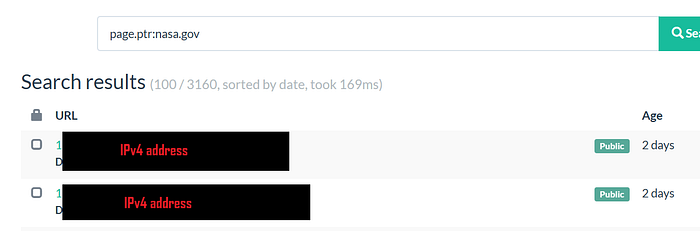
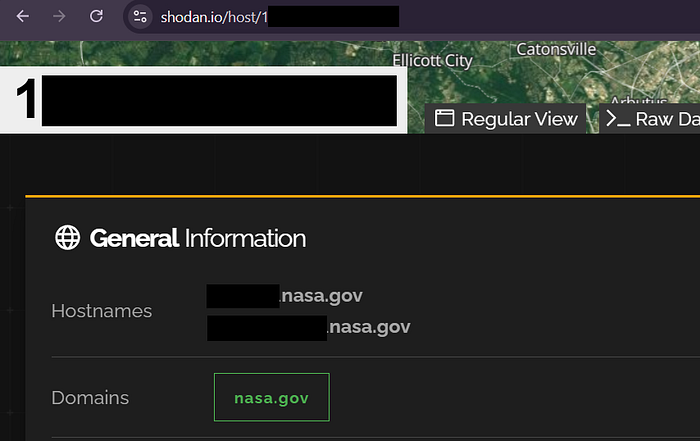
Now search this IP using shodan at https://shodan.io/host/<ipv4>
This can help to find untouched endpoints in big organizations & companies who has own IP/network : subnet/range and not borrowing from Cloud belonging to other providers.
Never forget vhost discovery 🤘
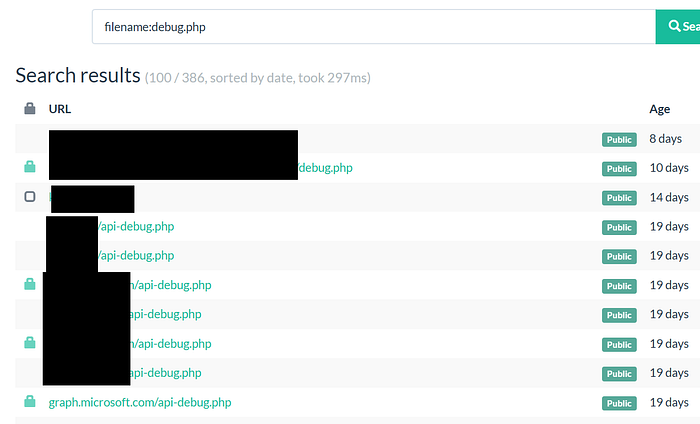
5️⃣ Filename Search Operator
filename:setup-config.php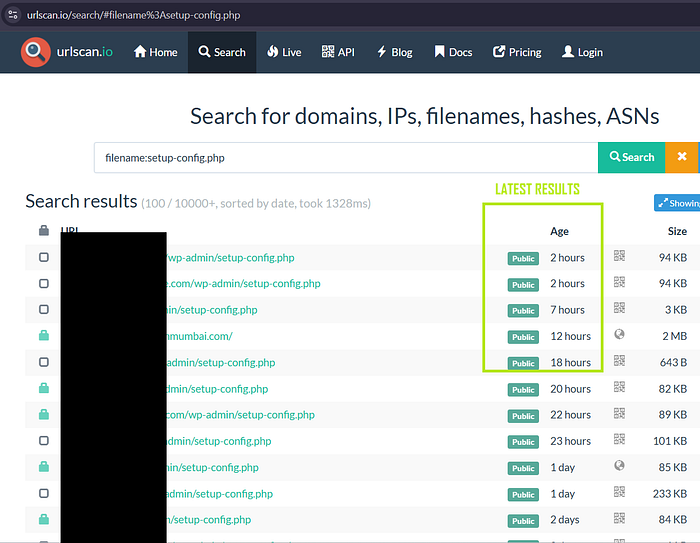
filename:phpinfo.php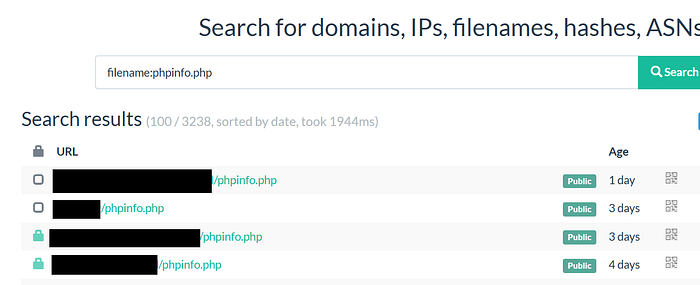
filename:debug.php
filename:install.php